Security Analysis is only available on PRO plan.
Static Code Analysis
Understand the security vulnerabilities in your code at multiple levels from SQL injection to XSS and more with Code-Suggestion fixes.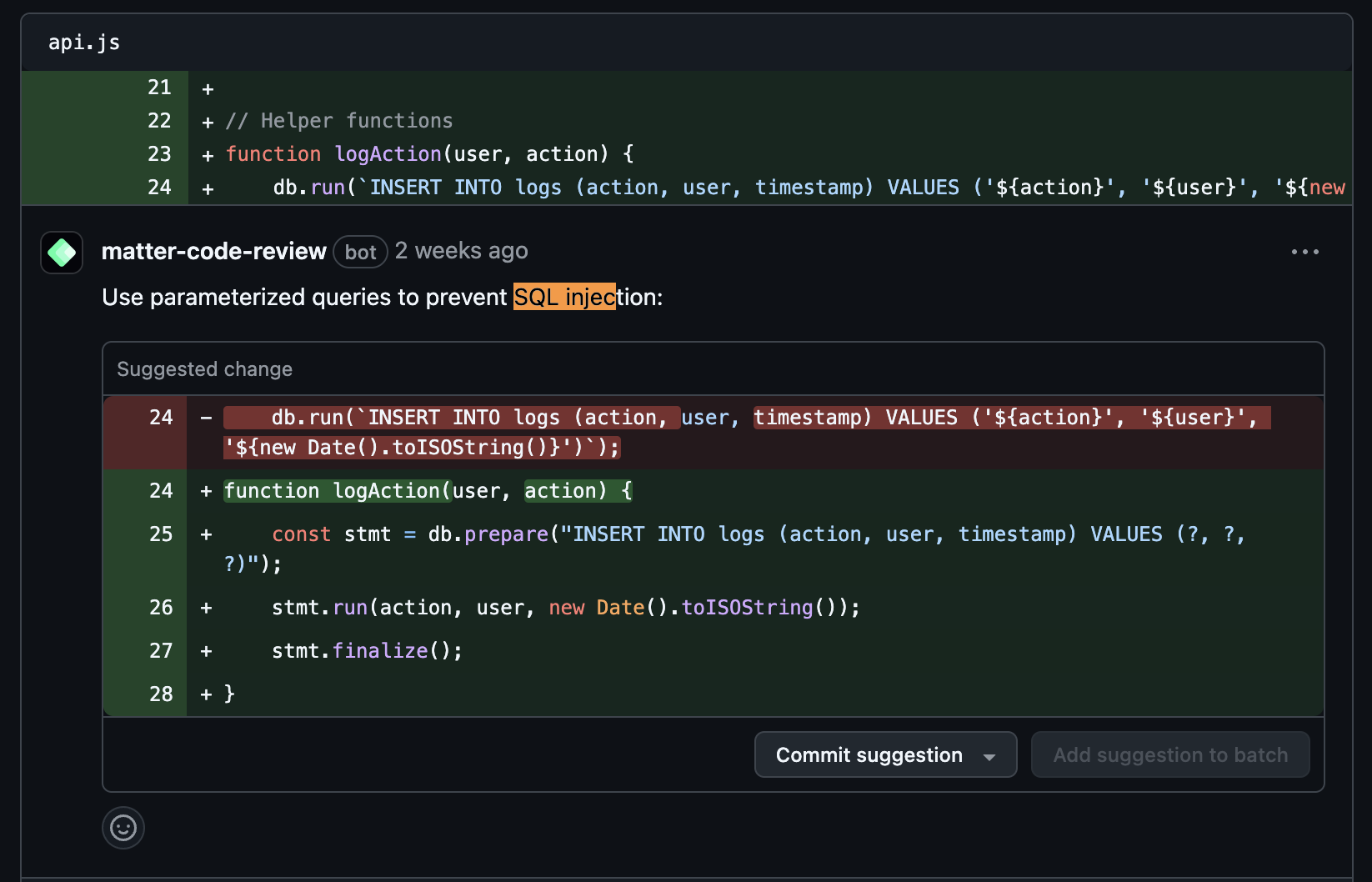
Some examples
Input Validation Issues
Input Validation Issues
- Lack of proper input sanitization leading to injection attacks
- Failure to validate file paths or file contents before processing
Authentication and Authorization Flaws
Authentication and Authorization Flaws
Documentation Content Security
Documentation Content Security
- Cross-site scripting (XSS) vulnerabilities when displaying user-contributed code examples
- Missing content security policies for rendered documentation
Data Handling Issues
Data Handling Issues
- Leakage of sensitive information in error messages or logs
- Insecure storage of user preferences or documentation settings
Integration Vulnerabilities
Integration Vulnerabilities
- Insecure communication with code repositories or analysis backends
- Path traversal vulnerabilities when importing external content
Configuration Management
Configuration Management
- Insecure default settings that expose sensitive analysis results
- Insufficient protection of configuration files containing sensitive information
Third-Party Dependencies
Third-Party Dependencies
- Use of outdated libraries with known vulnerabilities
- Insufficient validation of plugin or extension integrity
Package Vulnerabilities Detection
Understand the package vulnerabilities in your Pull Requests and get fixes with recommendation versions.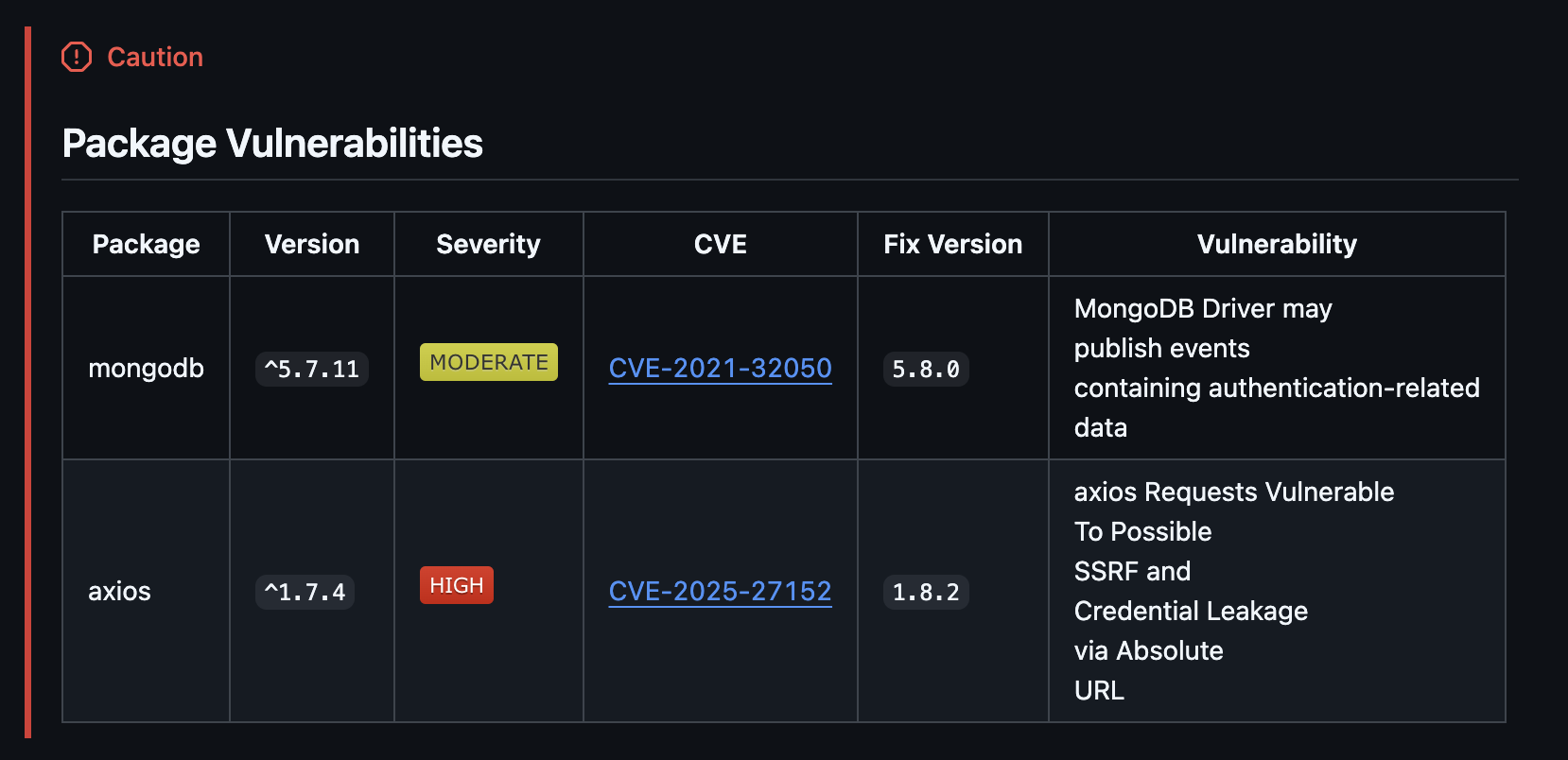
Some examples
Third-Party Dependencies
Third-Party Dependencies
- Use of outdated libraries with known vulnerabilities